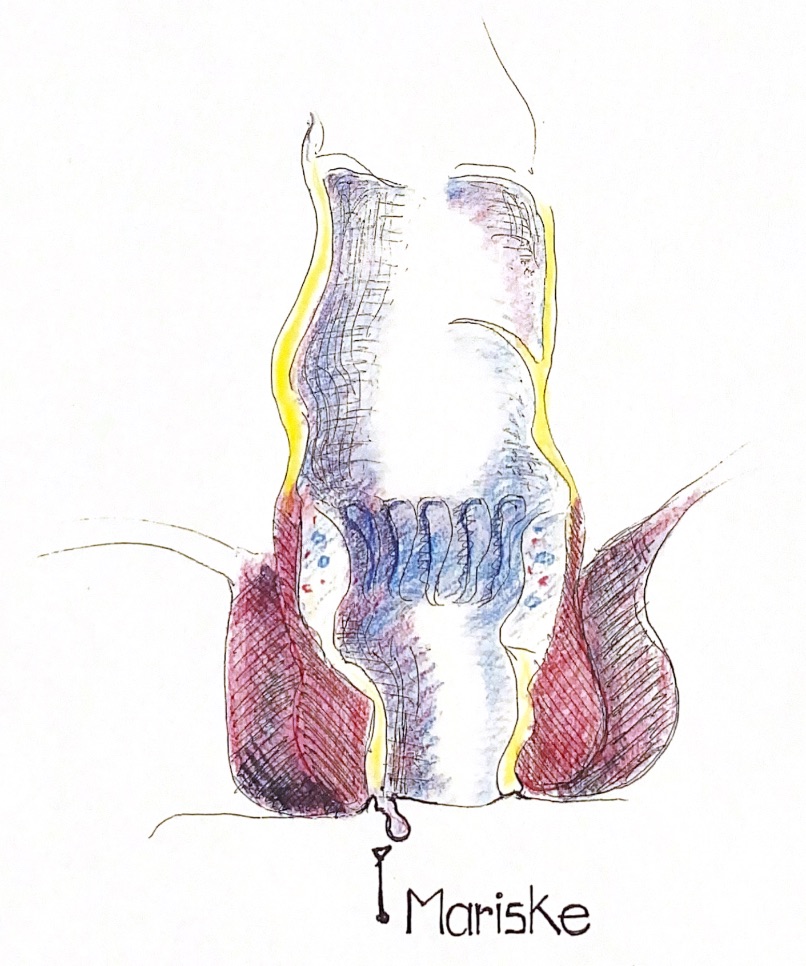
Marisken
Marisken sind vergrößerte Hautfalten am Rand des Afters.
Sie entstehen manchmal nach Schwangerschaften oder Analvenenthrombose. Oft ist die Ursache unklar.
Sie machen kaum Beschwerden (Brennen, Anschwellen) und sind harmlos. Häufig Schwellungen können ein Hinweis auf ein Haemorrhoidalleiden oder auf eine Analfissur sein, welche behandlungsbedürftig sind.
Sollten Marisken aus „hygienischen Gründen“ stören, besteht die Möglichkeit, diese operativ zu entfernen.